 Many employees tend to overlook physical security measures in their workplace and lack awareness of the facility’s access control system. Upon starting a new job, most workers receive a badge, accompanied by instructions from the security staff to keep it visible during work hours. From there, they are shown to expect that secure doors and vehicle gates will magically unlock or open when they present their badge. The extent of employee involvement in security ends at reporting lost badges, ensuring no one follows them into the building, and occasionally scanning their badge when leaving work.
Many employees tend to overlook physical security measures in their workplace and lack awareness of the facility’s access control system. Upon starting a new job, most workers receive a badge, accompanied by instructions from the security staff to keep it visible during work hours. From there, they are shown to expect that secure doors and vehicle gates will magically unlock or open when they present their badge. The extent of employee involvement in security ends at reporting lost badges, ensuring no one follows them into the building, and occasionally scanning their badge when leaving work.
While employees only see the system’s surface level, the physical access control system (PACS) involves a sophisticated network of components. The system can also come with potential vulnerabilities and gaps in security. In this blog, we’ll go over the common security gaps and practical solutions. If you’ve ever wondered what goes on beyond the badge, or if you’re a security professional looking to achieve better control over your PACS, then this blog is for you.
The Inner Workings
The main components of an access control system comprise of the following:
- Employee Security Badges
- Security Badge Readers
- Access Control Panels
- Door Locks
- Access Control Software
- Security Access Control Database
Badges or credentials can take various forms, including access cards, key fobs, or mobile credentials linked to phones, each using diverse technologies and security measures. Readers, responsible for matching badge technology, are not confined to fixed door readers alone; they can be found on desktop readers activating computers and handheld badge and biometric readers. In addition, keypads, various door lock hardware, alarm systems, door control panels, access control software, and the intricate networking and wiring that connect them all contribute to the complexity of the access control system.

While the physical access control system is intricate and expensive, it adds substantial value to the company’s overall physical security.
When a worker scans their badge to access a door, the backend process unfolds in the following manner: The reader transmits the badge number to a concealed access panel, which then verifies the recorded access permissions. If valid, the door opens almost immediately. Subsequently, the panel sends the badge number, permissions, and door information to the backend access control system database. From an employee’s perspective, the crucial aspect is the swift opening of the door. If it takes longer than about one second, employees will feel that there is something wrong with the system.
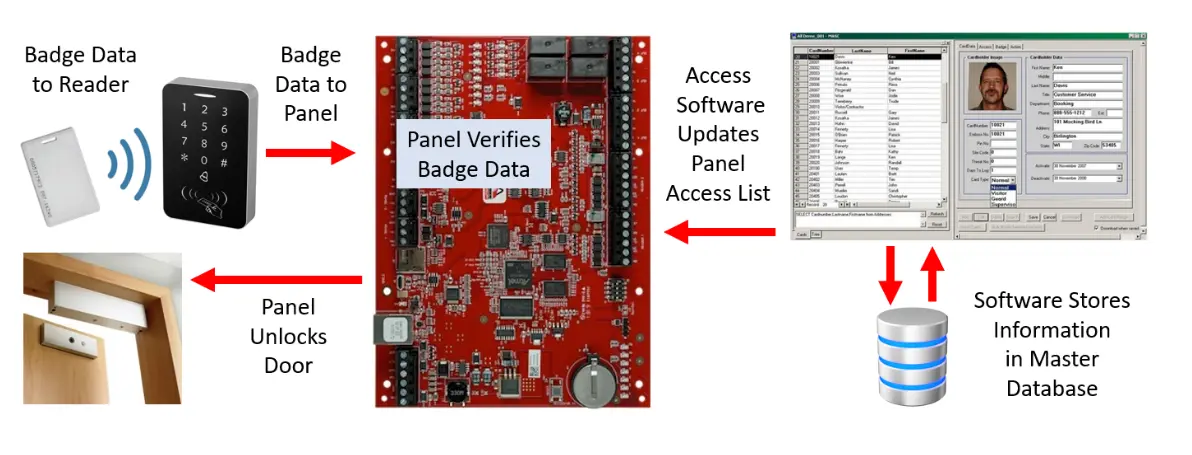
Within the backend access control system, all information is documented as either ENTRY or EXIT events in the access control database. The activity data stored in these systems is relatively straightforward, resembling the following format:
| Event Description | Time / Date | Device # | Badge # |
| Entry Granted | 8:04AM 1/19/2024 | B2D1 | 3074 |
| Entry Granted | 7:57AM 1/19/2024 | B2D1 | 3176 |
| Entry Granted | 7:42AM 1/19/2024 | Y1G1 | 4203 |
| Entry Denied | 7:41AM 1/19/2024 | B2D1 | 3875 |
| Entry Granted | 7:40AM 1/19/2024 | B1D1 | 2787 |
| Entry Granted | 7:40AM 1/19/2024 | B1D1 | 1632 |
In other words, the access control system possesses information about the scanned badge, the permission status (access granted or denied), the timestamp, and the location of badge reading—an apparently robust system. However, several gaps undermine its completeness.
Notably, the system lacks knowledge of the badge holder’s identity. If an employee were to give their badge to someone else, that person could gain entry to the company premises without being an employee. Moreover, once a door is opened using a badge, there’s a vulnerability to tailgating, where others can easily follow behind. This risk is particularly pronounced with elevators. Additionally, employees often neglect to badge out upon leaving or may exit through a non-audited door, introducing further challenges to the system’s comprehensive security measures. Let’s talk about these gaps one at a time.
Gaps in the PACS

Is the right person in possession of the badge?
Determining whether the correct individual holds the badge poses a challenge. When a badge is scanned for entry into a secure facility, security personnel cannot confirm if it belongs to the person presenting it. Unfortunately, this verification is not possible without employing additional tools.
Workers exchanging or scanning a co-worker’s badge is not uncommon and presents a genuine concern, particularly when the access control system is utilized for tracking work hours (time and attendance). Additionally, the risk exists that a lost badge could be discovered by someone with malicious intent, allowing unauthorized access to a facility.
What about tailgating?
Let’s consider the phenomenon of tailgating or piggybacking—an infringement on physical security where an unauthorized person gains access to a secured facility by following an authorized individual. Essentially, a worker scans their badge to open a door and accesses the facility, but then holds the door open for others to enter without proper authorization. While the act of holding doors open for others may seem courteous, tailgating poses a significant security concern as it undermines the established security protocols in place to ensure workplace safety.
Did workers badge out when leaving?
 This is a crucial aspect for maintaining up-to-date occupancy information. If readers are installed at all exits and security professionals enforce the practice of badging out, it becomes a very valuable data point. It allows security professionals to have an accurate count of who is currently onsite and who has left (facility occupancy).
This is a crucial aspect for maintaining up-to-date occupancy information. If readers are installed at all exits and security professionals enforce the practice of badging out, it becomes a very valuable data point. It allows security professionals to have an accurate count of who is currently onsite and who has left (facility occupancy).
Regrettably, numerous sites have back exit doors that do not require badging to exit, potentially leading to inaccuracies in the occupancy count. This becomes particularly significant in ensuring the safety of employees in an evacuation and emergency mustering. The absence of this information may leave safety professionals, such as Fire Wardens, Emergency Managers, Evacuation Officers, or Crisis Managers, uncertain about whether everyone has indeed evacuated a facility during a fire or other emergency event and accounted for as safe.
Gain Better Control Over Your Access Control
These gaps present a significant challenge for businesses on various fronts. From a physical security perspective, the ability to control access to the premises diminishes. Borrowing a badge or tailgating to enter another workspace to check out equipment, use the bathroom, enjoy lunch at a superior cafeteria, or explore a secured area raises concern.
 The situation escalates when someone intends to steal equipment, intellectual property, or trade secrets. Once an unauthorized entry breaches the perimeter, the potential damage is considerable. The intruder gains unrestricted access to secured workspaces, and guards face challenges in swiftly verifying permissions, exacerbating the security risks.
The situation escalates when someone intends to steal equipment, intellectual property, or trade secrets. Once an unauthorized entry breaches the perimeter, the potential damage is considerable. The intruder gains unrestricted access to secured workspaces, and guards face challenges in swiftly verifying permissions, exacerbating the security risks.
Manned handheld badge readers integrated with the physical access control system offer a comprehensive solution to these challenges. Mirroring the functionalities of a fixed door reader, a handheld, mobile device to read badges or biometrics enables security professionals to:
- Track entries and exits when a badge reader at a door goes down or is under maintenance
- Perform on-the-go validation from anywhere
- View information from the access control system, such as an ID number, name, and photo, right on the device to verify the identity of the badge holder
This ensures that only the correct individual is granted admission into the facility. Moreover, the handheld scanning of each badge eliminates the possibility of tailgating, enhancing security measures and preventing unauthorized access.
Handheld Solutions from Telaeris
Explore the capabilities of XPressEntry handheld badge and biometric readers from Telaeris, the handheld solution for access control systems. XPressEntry is a powerful tool that offers exceptional flexibility and encompasses all the functionalities previously described.
XPressEntry empowers security and safety professionals to:

- Validate credentials or biometrics against the identity information on record in the access control system database from anywhere
- Record entries and exits where door readers are not practical or available
- Challenge credentials from within secured spaces
- Spot check permissions to deter tailgating / piggybacking
- Quickly muster employees during an emergency evacuation
- Maintain facility occupancy information
- and so much more!
Additionally, XPressEntry handheld readers proudly lead the industry with the most access control integrations and the broadest support for badge technologies and biometrics.
Don’t have a physical access control system (PACS) onsite? No problem. XPressEntry also works as a stand-alone solution, fully managed by the XPressEntry Server.
CONTACT US for more information and a demo.
